Security Information and Event Management (SIEM) is a must-have tool for modern cybersecurity. It helps businesses spot, monitor, and handle security threats quickly. If you’re new to SIEM, understanding how it works and how it boosts your security system is essential. This guide will walk you through everything you need to know about SIEM, whether you’re just starting or looking to upgrade your current system.
What is SIEM?
SIEM stands for Security Information and Event Management. It combines two key functions—Security Information Management (SIM) and Security Event Management (SEM).
SIM:
-
Collects and stores log data from various systems.
SEM:
-
Monitors and responds to security events in real-time.
Together, these functions allow SIEM to provide threat detection, real-time alerts, and compliance support, all in one platform.
The 2025 SIEM Guide
Best SIEM Tools for Threat Detection
Selecting the right SIEM tool is vital for effective threat detection and response. Below are the top SIEM tools for 2025:
| Tool | Feature | Best For |
|---|---|---|
| Splunk | Great for log management | Large companies |
| Elastic SIEM | Open-source, scalable | Small to medium-sized businesses |
| LogRhythm | Good analytics and reporting | Compliance-heavy industries |
| IBM QRadar | AI-powered security | Large, complex businesses |
| SolarWinds | Easy setup, affordable | Small businesses |
Each tool has unique strengths, so it’s important to choose the one that best fits your company’s size and needs.
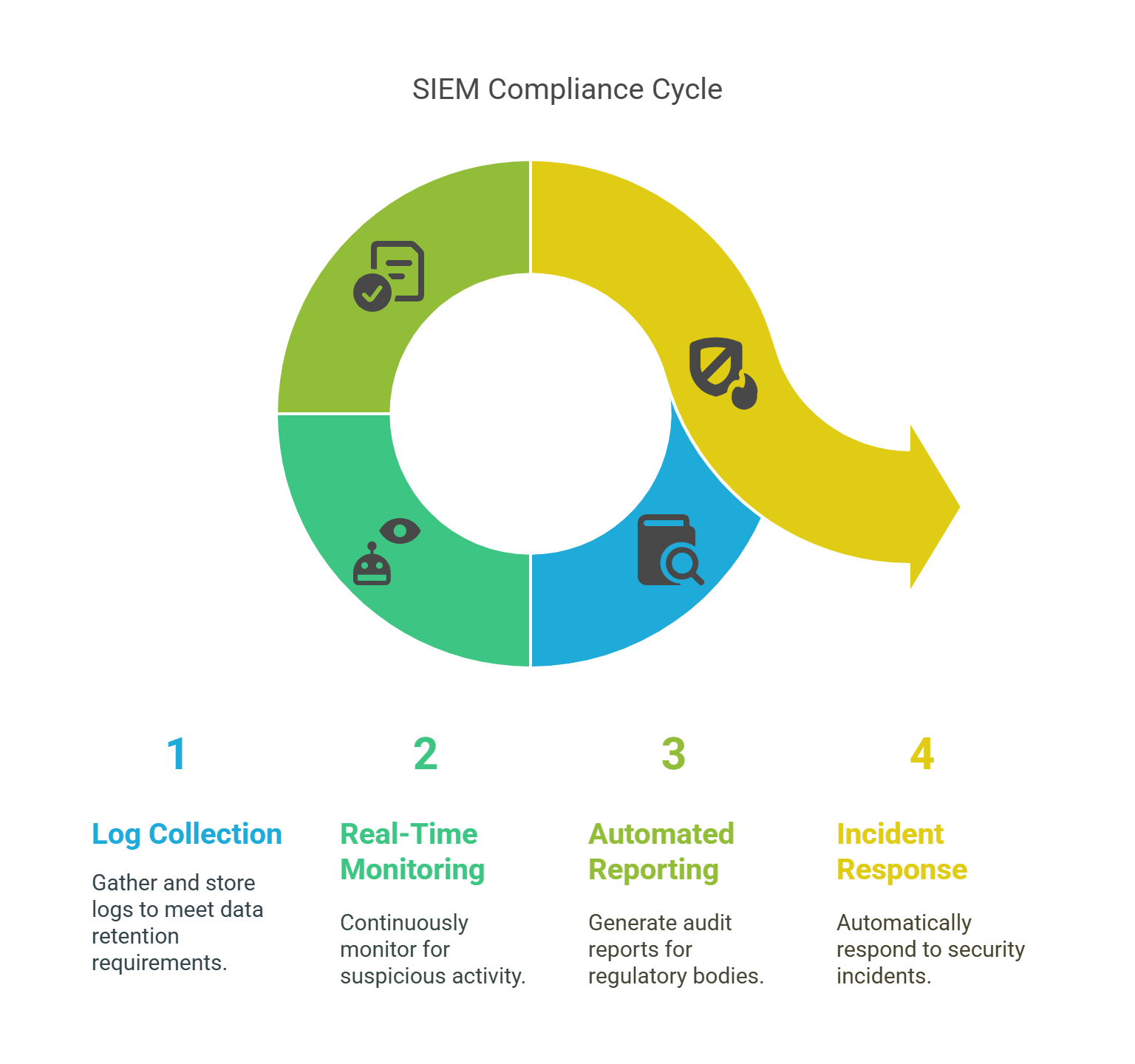
How SIEM Improves Compliance
SIEM helps businesses comply with regulations like GDPR, HIPAA, and PCI-DSS. Here’s how:
-
Log Collection: SIEM stores logs, helping you meet regulatory data retention requirements.
-
Real-Time Monitoring: Continuous monitoring alerts you to suspicious activity, helping ensure compliance.
-
Automated Reporting: SIEM generates audit reports that can be shared with regulatory bodies.
-
Incident Response: Many SIEM tools automatically respond to security incidents, reducing the risk of penalties.
SIEM vs. SOAR: Key Differences
While both SIEM and SOAR (Security Orchestration, Automation, and Response) are important for cybersecurity, they serve different functions. Let’s compare:
| Feature | SIEM | SOAR |
|---|---|---|
| Function | Logs and monitors security events | Automates incident response |
| Benefit | Detects threats across your network | Speeds up incident response |
| Best Use | Detects and alerts on events | Manages incident containment |
SIEM handles threat detection, while SOAR automates responses to limit the damage from security incidents.
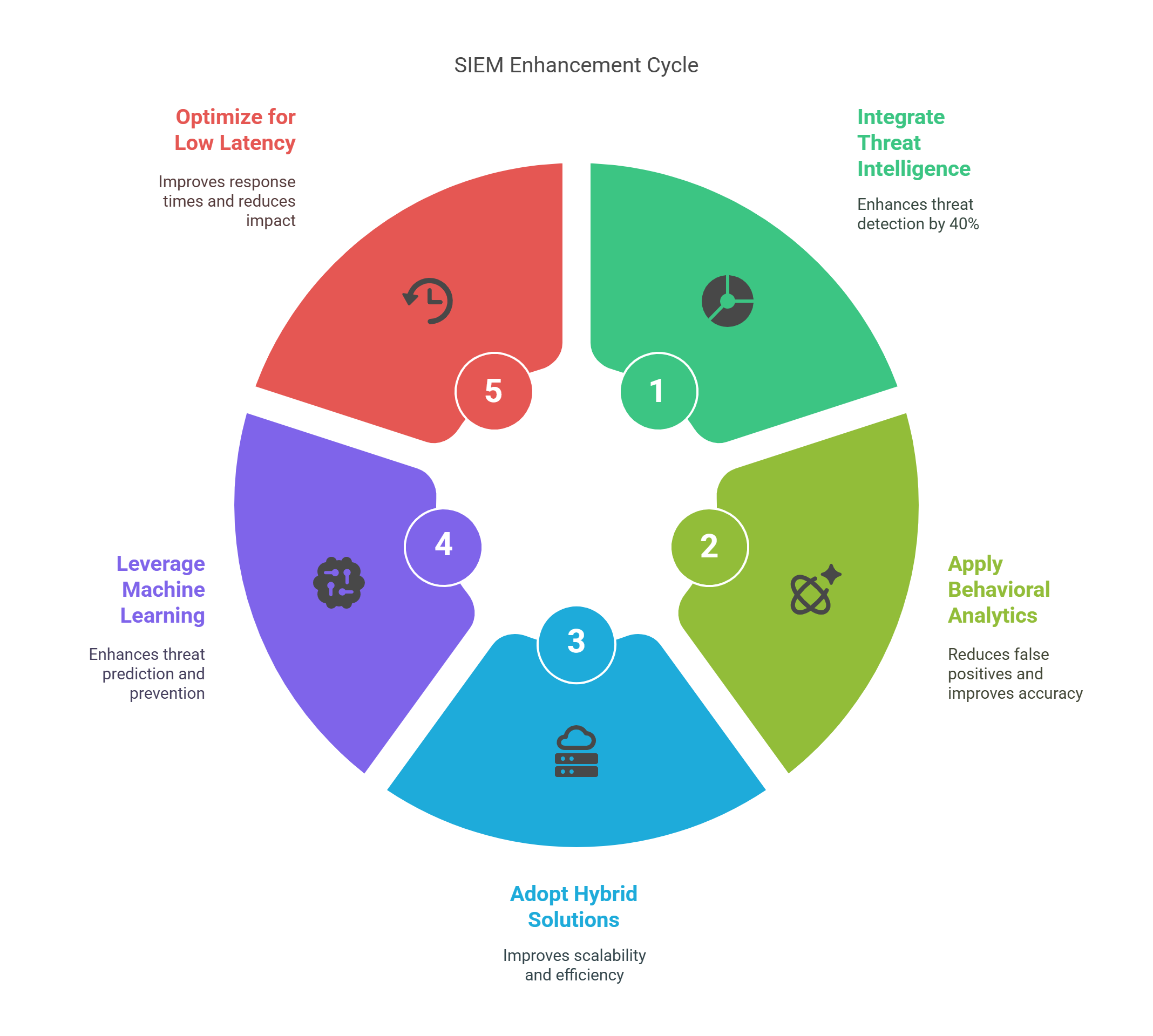
5 Research-Backed Strategies for SIEM in 2025
Here are five proven strategies to enhance your SIEM system:
1. Add Threat Intelligence Feeds
-
Studies show that integrating threat intelligence improves threat detection by 40%.
2. Use Behavioral Analytics
-
Research shows that behavioral analytics reduce false positives by 30% and enhance detection accuracy.
3. Adopt Hybrid SIEM-Cloud Solutions
-
Combining on-premise and cloud systems improves scalability and efficiency.
4. Leverage Machine Learning
-
Machine learning makes SIEM systems 60% better at predicting and preventing future threats.
5. Optimize for Low Latency
-
Keeping latency under 100ms helps improve response times, reducing overall threat impact.
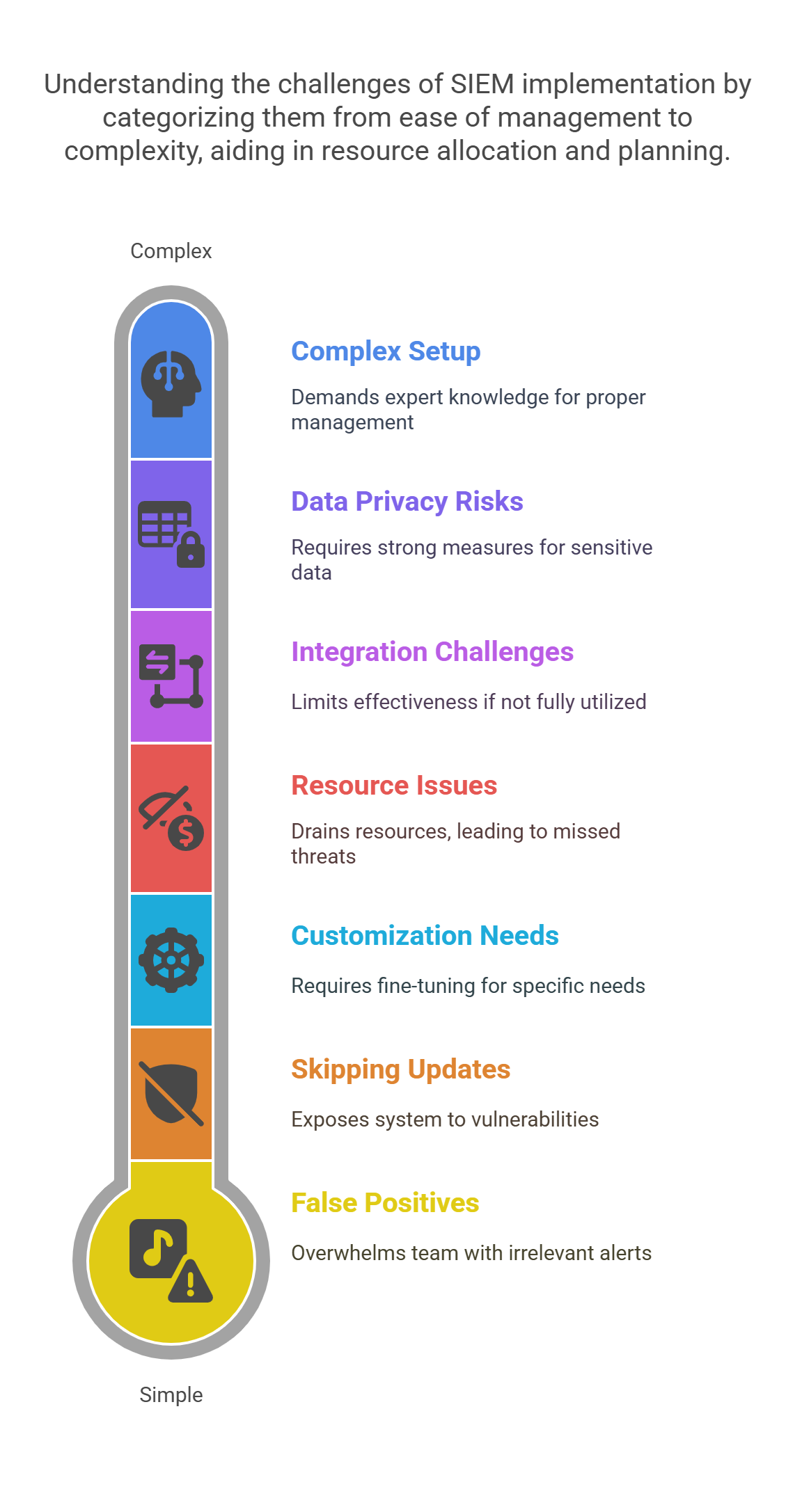
7 Hidden Dangers of SIEM You Must Avoid
While SIEM is a powerful tool, it comes with its own challenges. Here are seven potential dangers:
1. False Positives
-
Too many false alerts can overwhelm your team, slowing down response times.
2. Customization Needs
-
Default settings might not be ideal for your company’s specific security needs. Customizing your SIEM tool is important.
3. Resource Issues
-
SIEM tools require substantial resources. Insufficient resources can lead to missed threats.
4. Data Privacy Risks
-
SIEM handles sensitive data, so it’s important to implement strong data protection measures to stay compliant with privacy laws.
5. Complex Setup
-
Some SIEM tools are difficult to set up and require expert knowledge to manage them properly.
6. Integration Challenges
-
Many SIEM platforms offer integrations, but if they’re not fully utilized, their effectiveness may be limited.
7. Skipping Updates
-
Regular updates are necessary to protect against new threats. Neglecting updates can make your system vulnerable.
Expert Predictions for SIEM in 2025
The future of SIEM is closely tied to advancements in AI and machine learning. Here are some trends to watch for in 2025:
-
AI-Powered Detection: Machine learning will improve the accuracy of threat detection, reducing false positives.
-
Cloud-Native SIEM: More businesses will move to cloud-based SIEM systems for better flexibility and scalability.
-
SOAR Integration: SIEM systems will increasingly integrate with SOAR platforms, allowing for faster response times and better incident management.
-
Automated Compliance: As regulations grow, SIEM systems will automate the process of generating compliance reports, making it easier to stay up to date with requirements.
FAQs
Q1: What is the purpose of SIEM?
A1: SIEM helps organizations collect, analyze, and monitor security event data to detect potential threats and respond quickly.
Q2: How does SIEM differ from SOAR?
A2: SIEM focuses on detecting and logging security events, while SOAR automates the response to these incidents, speeding up remediation.
Q3: Can small businesses benefit from SIEM?
A3: Yes, small businesses can benefit from affordable, open-source SIEM solutions that offer real-time monitoring, compliance, and threat detection.
Q4: Are there free SIEM tools available?
A4: Yes, there are open-source SIEM tools like Elastic SIEM and OSSIM, which offer powerful features without the high cost of commercial solutions.
Your Custom SIEM Implementation Plan
Here’s a step-by-step plan to implement SIEM in your organization:
Step 1: Set Clear Security Goals
-
Determine what types of threats you need to monitor and the regulations you need to comply with.
Step 2: Choose the Right SIEM Tool
-
Pick a SIEM solution that fits your business size, budget, and security needs.
Step 3: Connect Your Systems to SIEM
-
Integrate firewalls, servers, applications, and cloud environments into your SIEM system for comprehensive monitoring.
Step 4: Set Up Real-Time Alerts
-
Set up alerts to notify your team immediately when a security event is detected.
Step 5: Test Your SIEM Regularly
-
Regularly test the system to ensure it is detecting and responding to threats as expected.
Conclusion
SIEM is a powerful tool that can significantly improve your organization’s cybersecurity by providing real-time monitoring, detecting threats, and ensuring compliance. By selecting the right SIEM tool, integrating it into your systems, and optimizing it for efficiency, you can enhance your security infrastructure and protect your business. Start using SIEM today to strengthen your cybersecurity defenses and stay ahead of evolving threats.


