As businesses shift to the cloud, securing sensitive customer data in public cloud SaaS applications becomes essential. Whether you’re a SaaS provider or use cloud services, protecting your data from cyber threats, unauthorized access, and breaches is critical. In this article, we’ll cover the best practices for keeping your customers’ data safe and compliant while maintaining cloud performance.
Why Securing Sensitive Customer Data is Crucial in Cloud SaaS
Cloud computing offers great benefits like cost savings and scalability, but it also introduces risks. Sensitive data such as financial details, personal info, and health records is vulnerable in the cloud. A data breach could lead to major financial losses, damage to your reputation, and legal trouble. Therefore, securing sensitive data in public cloud SaaS apps is vital.

5 Key Strategies for Securing Sensitive Data in Cloud SaaS
Here are five proven strategies to protect sensitive customer data in the cloud.
1. Data Encryption
Encryption is one of the best ways to keep sensitive data safe. It ensures that data is unreadable to anyone without the correct decryption key, whether it’s stored or being transferred.
-
Best Practice: Use end-to-end encryption to protect data on both ends of communication.
2. Multi-Factor Authentication (MFA)
MFA strengthens security by requiring two or more forms of identification, such as passwords, security tokens, or biometrics. This reduces the risk of unauthorized access.
-
Best Practice: Make MFA mandatory for all users, especially those with admin access.
3. Data Backup and Disaster Recovery Plans
Having a backup plan ensures that, in case of an attack or failure, your sensitive data can be quickly restored. Many cloud providers offer automatic backup services, but make sure these backups are encrypted and tested regularly.
-
Best Practice: Set up automatic backups and test your recovery process frequently.
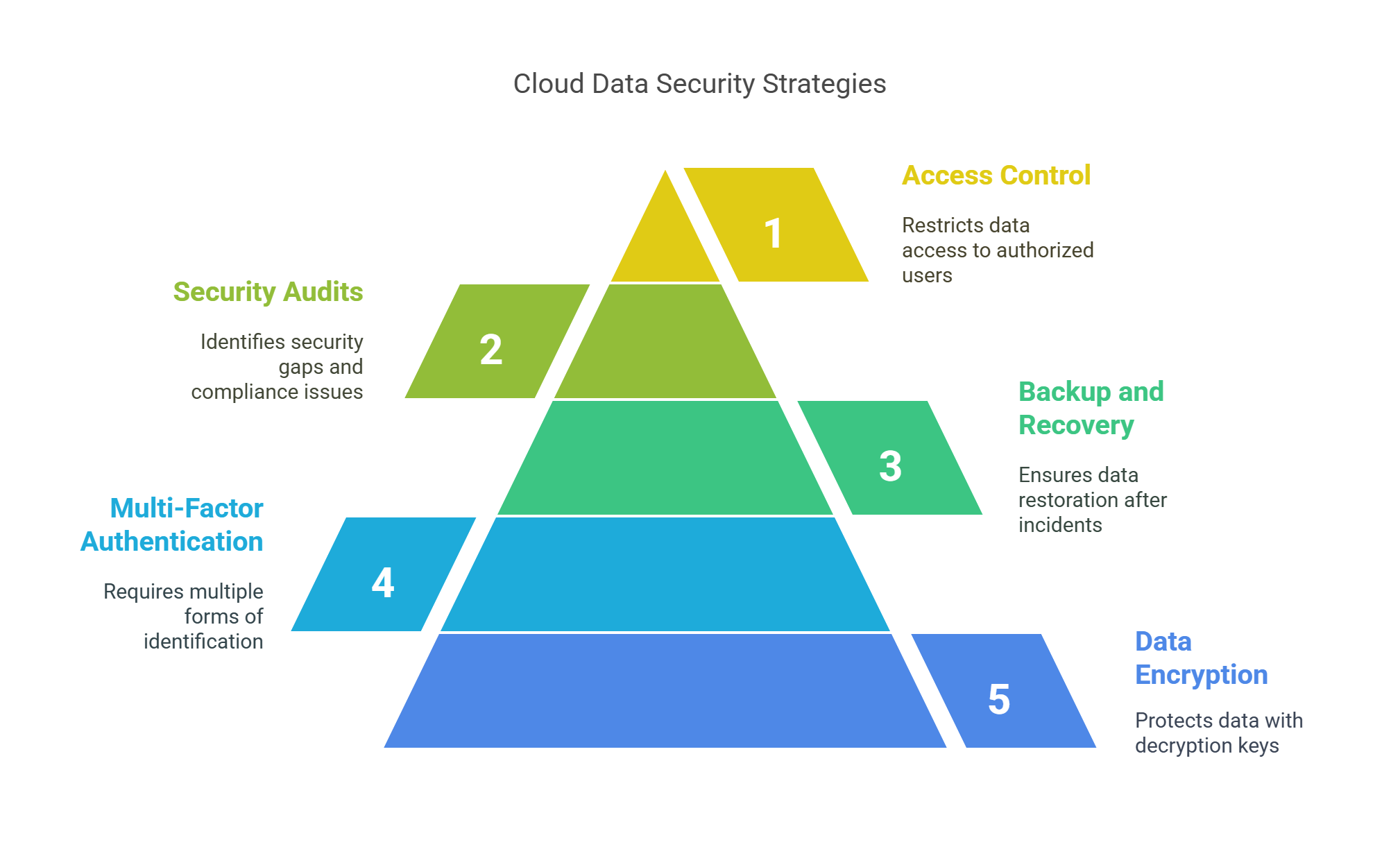
4. Regular Security Audits and Monitoring
Regular audits and continuous monitoring are essential for spotting security gaps before they lead to a breach. Security audit tools help identify misconfigurations and compliance issues.
-
Best Practice: Conduct regular scans and use real-time monitoring to detect any unusual activities.
5. Data Access Control and Role-Based Permissions
Enforcing strict access control ensures that only authorized users can view sensitive data. Role-based access control (RBAC) lets you assign specific permissions to users, reducing exposure to data breaches.
-
Best Practice: Apply the principle of least privilege, allowing users only the access they need for their roles.
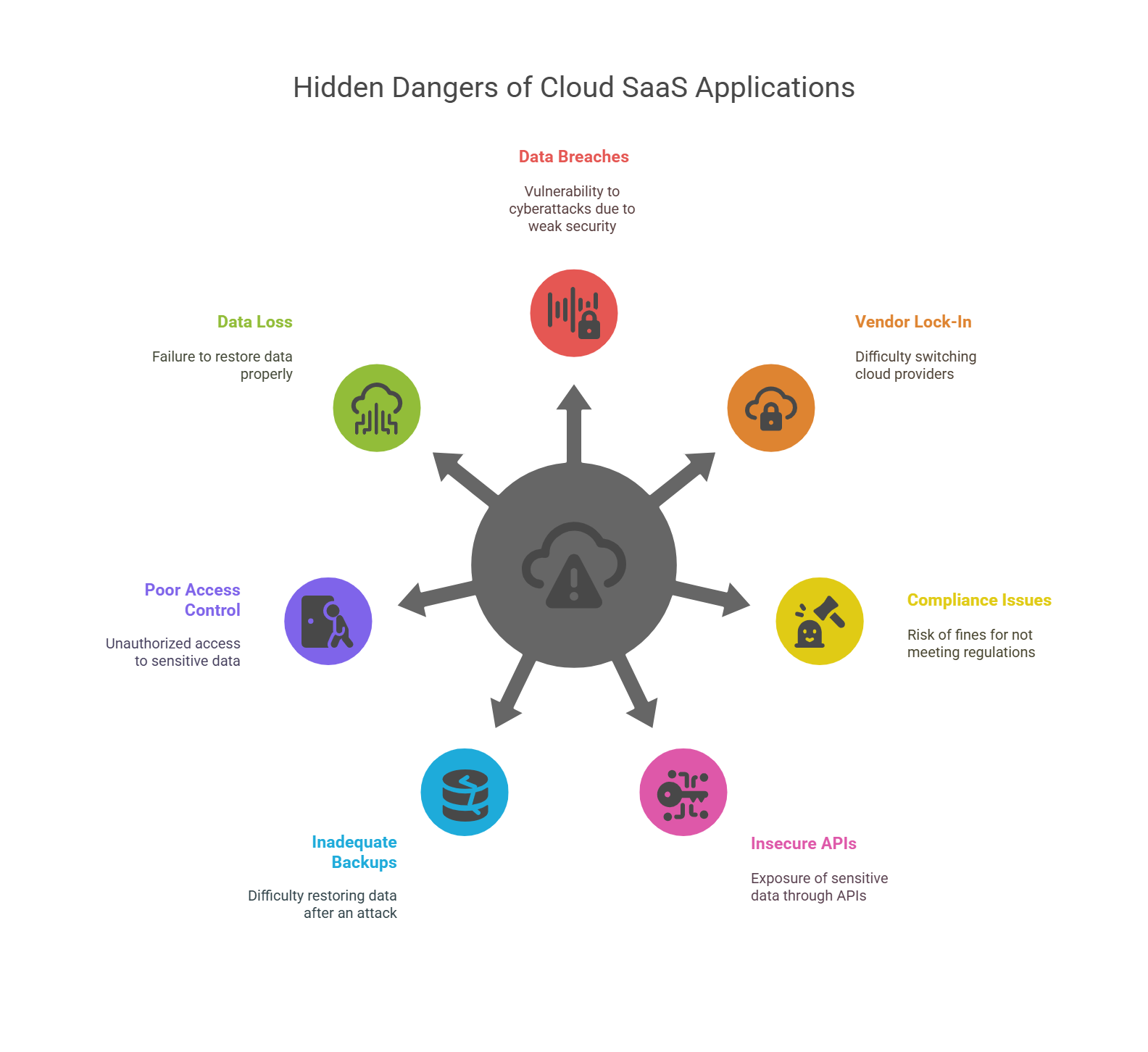
7 Hidden Dangers of Public Cloud SaaS Applications
While the cloud has many benefits, there are some hidden dangers businesses need to be aware of.
-
Data Breaches: Misconfigurations and weak security make cloud environments vulnerable to cyberattacks.
-
Vendor Lock-In: Relying on one cloud vendor can make it difficult to switch providers.
-
Compliance Issues: Failing to meet regulations like GDPR or HIPAA can result in fines.
-
Insecure APIs: Poorly secured APIs may expose sensitive data to unauthorized access.
-
Inadequate Backups: If backups are not secure, restoring data after an attack becomes difficult.
-
Poor Access Control: Mismanaged permissions can lead to unauthorized access to sensitive data.
-
Data Loss: Cloud services might fail to restore data properly, even with backups.
Expert Predictions: The Future of Data Security in Cloud SaaS by 2025
Experts believe that data security will continue to evolve by 2025, with AI and machine learning playing a major role. These technologies will help detect threats, automate security measures, and respond to breaches in real-time.
-
Expert Opinion: “By 2025, AI-powered security measures will become standard, automatically detecting and responding to threats.”
5. FAQs
Q1: What is the best way to secure customer data in cloud SaaS applications?
A1: The best strategy is a multi-layered approach, including encryption, multi-factor authentication, data backups, and access control.
Q2: How does encryption protect sensitive data in SaaS applications?
A2: Encryption converts data into a format that only authorized users can read, keeping it safe from unauthorized access.
Q3: What happens if sensitive data isn’t secured in the cloud?
A3: If not secured, sensitive data is at risk of breaches, legal penalties, loss of trust, and financial losses.
Q4: How often should I conduct security audits for my cloud services?
A4: Security audits should be conducted quarterly, with continuous monitoring to detect security vulnerabilities.
Comparison Tables
1. Encryption vs. Tokenization: Which Is Better for Data Security?
| Feature | Encryption | Tokenization |
|---|---|---|
| Security Level | High | High |
| Performance Impact | Can slow down operations if not optimized | Typically faster in processing |
| Cost | Higher due to cryptographic systems | Lower, but requires a secure token vault |
| Usage | Best for securing data during transfer | Best for reducing data exposure |
2. MFA vs. Password-Based Authentication: Comparison
| Feature | MFA | Password-Based Authentication |
|---|---|---|
| Security Level | Very High (multi-layered security) | Low (vulnerable to password theft) |
| User Experience | Slightly inconvenient for users | Simple but less secure |
| Cost | Higher due to setup and maintenance | Low, built into most systems |
3. RBAC vs. ABAC: Which One Is Right for Your Business?
| Feature | RBAC | ABAC |
|---|---|---|
| Flexibility | Limited to user roles | Flexible, based on attributes |
| Complexity | Simpler to implement and manage | More complex, requires advanced policies |
| Security | Effective for basic access management | More granular and dynamic control |
Conclusion
Securing sensitive customer data in public cloud SaaS applications is essential for protecting your business from data breaches and legal consequences. By using best practices like data encryption, multi-factor authentication, and regular audits, you can create a secure environment for your customer’s data. Implementing these strategies reduces risks and builds customer trust. As AI and machine learning continue to advance, businesses will stay ahead of new threats in 2025 and beyond.