Healthcare organizations are using AWS (Amazon Web Services) because it offers flexibility, scalability, and cost savings. But when handling healthcare data, compliance with HIPAA (Health Insurance Portability and Accountability Act) is critical. HIPAA has strict rules on how sensitive data must be stored, shared, and protected. AWS needs to be set up correctly to follow these guidelines.
This post will guide you through the steps to ensure your AWS environment meets HIPAA standards. By the end, you’ll know what to do to protect Protected Health Information (PHI) and avoid penalties.
What is HIPAA?
HIPAA is a U.S. law that protects patient health information. It ensures sensitive data, like electronic health records (EHR), is not shared without the patient’s consent.
How Does AWS Help with HIPAA Compliance?
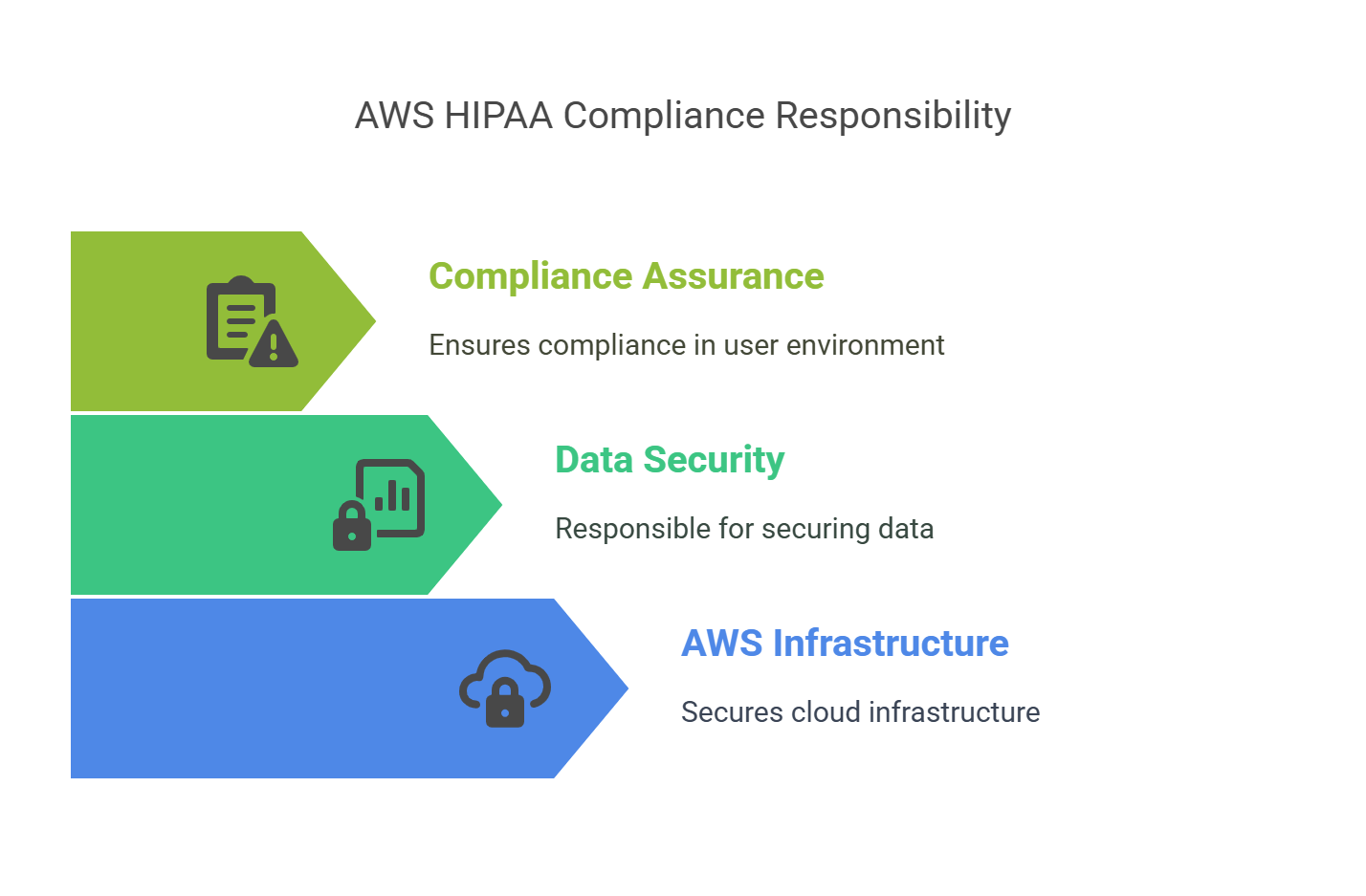
AWS offers services that can help meet HIPAA requirements. However, AWS uses a shared responsibility model. This means AWS secures the cloud infrastructure, but you are responsible for securing your data and ensuring compliance in your environment.
Cloud Compliance Checklist for HIPAA in AWS Environments
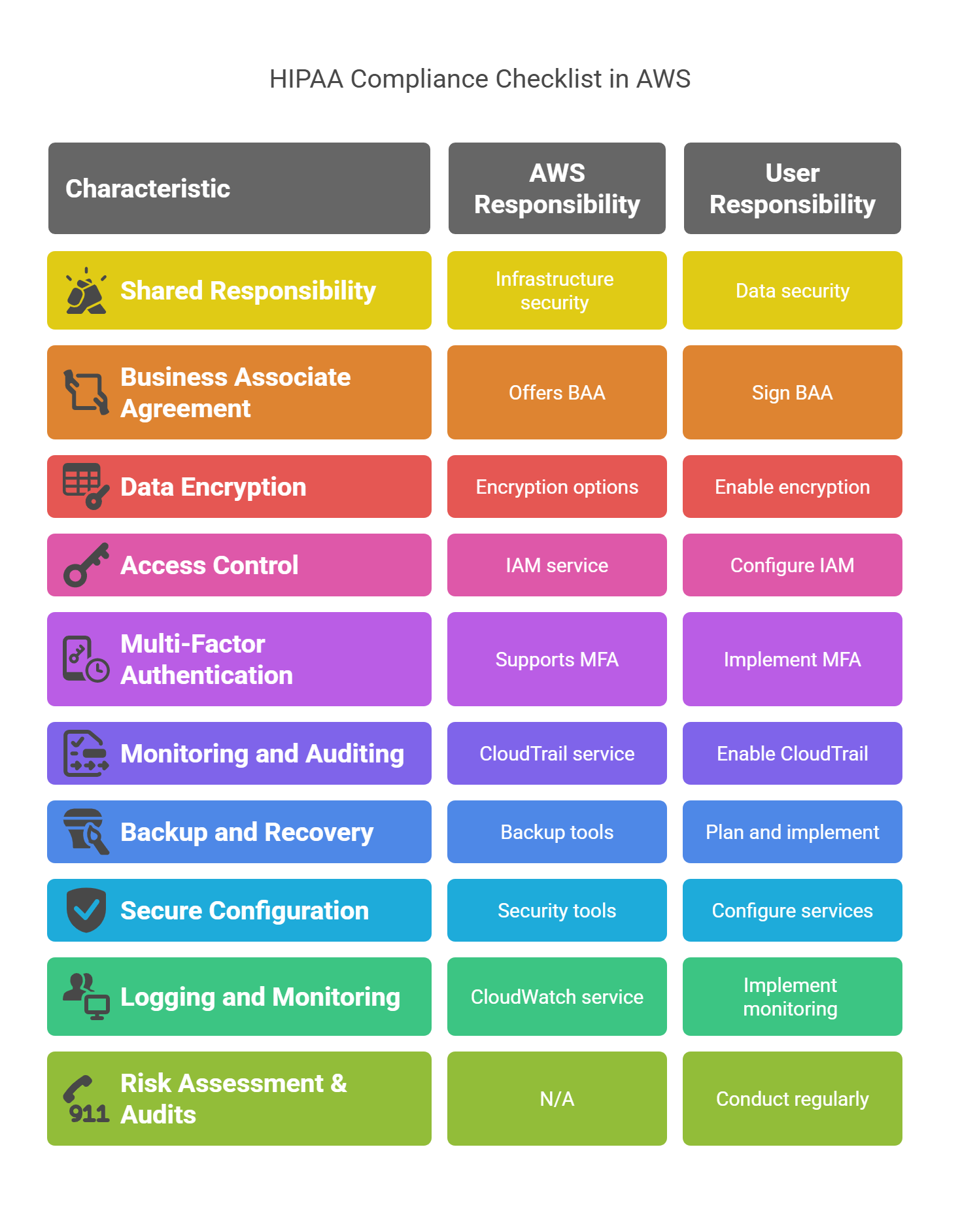
1. Understand the Shared Responsibility Model
AWS shares security responsibility with you. AWS manages the cloud infrastructure, while you manage your data’s security.
Why It’s Important:
Knowing what AWS secures and what you are responsible for is essential. Failing to secure your data could lead to a breach and severe penalties.
2. Sign a Business Associate Agreement (BAA) with AWS
HIPAA requires a Business Associate Agreement (BAA) when using third-party services like AWS to store or process PHI. AWS offers a BAA for services handling PHI.
Why It’s Important:
Without a signed BAA, using AWS for PHI is not HIPAA-compliant, which can lead to violations.
3. Enable Data Encryption at Rest and in Transit
HIPAA requires data protection at all times. AWS provides encryption options like AWS Key Management Service (KMS) for data at rest and in transit.
Why It’s Important:
Encryption protects PHI from unauthorized access, whether stored in Amazon S3, RDS, or moving across the network.
4. Control Access with IAM (Identity and Access Management)
Limit access based on who needs it. AWS IAM lets you create roles and policies to control who can access which data and resources.
Why It’s Important:
HIPAA requires that only authorized users can access PHI. IAM ensures access is restricted to the right people.
5. Implement Multi-Factor Authentication (MFA)
MFA adds extra security by requiring two or more methods of verification before granting access.
Why It’s Important:
MFA helps prevent unauthorized access, making it harder for hackers to get into your system.
6. Monitor and Audit Access with AWS CloudTrail
AWS CloudTrail tracks who accessed PHI and what changes were made. It logs all API calls for auditing and monitoring.
Why It’s Important:
HIPAA demands audit controls to track access to PHI. CloudTrail provides the necessary logging for HIPAA compliance.
7. Backup and Disaster Recovery Planning
Have a plan to restore your system quickly after a disaster. AWS tools like Amazon S3 and AWS Backup help ensure PHI is recoverable.
Why It’s Important:
HIPAA requires you to have a contingency plan to protect and recover PHI in case of emergencies.
8. Ensure Secure Configuration of AWS Services
AWS offers powerful tools, but these services must be securely configured to avoid exposing PHI.
Why It’s Important:
Misconfigurations are a common cause of data breaches. AWS provides tools like AWS Config and Trusted Advisor to ensure your configurations are secure.
9. Implement Logging and Monitoring with AWS CloudWatch
AWS CloudWatch provides metrics and logs to help you monitor the performance and security of your resources. Set up alerts for suspicious activities.
Why It’s Important:
HIPAA requires ongoing monitoring and responses to security incidents. CloudWatch helps you identify and fix issues before they compromise PHI.
10. Conduct Periodic Risk Assessments and Compliance Audits
Regular risk assessments and audits ensure your AWS environment stays HIPAA-compliant as your organization grows.
Why It’s Important:
HIPAA compliance is ongoing. Regular audits help maintain compliance over time.
FAQs
What are the key HIPAA requirements for AWS?
To ensure HIPAA compliance in AWS, you need to sign a BAA, encrypt data at rest and in transit, control access with IAM, and perform regular audits and monitoring. Periodic risk assessments are also important.
Is AWS HIPAA-compliant?
AWS offers HIPAA-eligible services, but it’s your responsibility to configure your AWS environment to comply with HIPAA guidelines.
What is the shared responsibility model in AWS?
AWS secures the infrastructure, while you are responsible for securing your data, managing user access, and ensuring compliance within your environment.
How can I ensure data is encrypted in AWS?
AWS provides encryption options like server-side encryption for data at rest and transport layer security (TLS) for data in transit. You can enable encryption for services like S3, RDS, and EBS.
Conclusion
Ensuring HIPAA compliance in AWS is essential for protecting patient data. By following this cloud compliance checklist, you can configure your AWS environment to meet HIPAA standards and protect PHI from unauthorized access. Always remember, securing your data is your responsibility. Understanding AWS’s shared responsibility model is crucial for achieving full compliance.
Take action now to secure your AWS environment and avoid the risks of non-compliance. If you need help, consider working with an expert in cloud compliance to ensure your environment stays secure.