In today’s world, keeping your network and data safe from cyber threats is very important. Cyberattacks are becoming more advanced, so both businesses and individuals need to use strong security systems. One of the most useful tools for protecting your data is the Intrusion Detection and Prevention System (IDPS).
What Is IDPS?
IDPS Explained
An Intrusion Detection and Prevention System (IDPS) is a tool that watches for suspicious activity on a network. It helps detect and stop unauthorized access, malware, and other dangers. When something unusual happens, it either alerts the administrators or blocks the threat right away.
The main goal of IDPS is to protect your systems by stopping hackers before they cause harm. It keeps an eye on your network and looks for signs of malicious activity before any damage happens.
Key Parts of an IDPS
-
Sensors: These watch different parts of the network and collect data to be analyzed.
-
Analysis Engine: This engine looks at the data and finds any potential threats.
-
Response Mechanism: If a threat is found, the IDPS can block it or send an alert.
Types of IDPS
There are different types of IDPS solutions. Each one works a bit differently. Here are the main types:
Network-Based IDPS (NIDPS)
Network-based systems monitor traffic on the network for suspicious activity. They check all traffic entering and leaving your network to find threats, like Distributed Denial of Service (DDoS) attacks.
Host-Based IDPS (HIDPS)
Host-based systems monitor individual devices, such as computers or servers. They look at activity on these devices and check for unusual behavior, like unauthorized file access.
Hybrid IDPS
Hybrid systems combine both network and host-based monitoring. They can detect a wider range of threats because they monitor both network traffic and device activity.
Signature-Based IDPS
Signature-based systems detect known threats using patterns, or “signatures,” from previous attacks. These systems are good at spotting familiar threats but may miss new or unknown ones.
Anomaly-Based IDPS
Anomaly-based systems look for anything that is unusual. They compare current activity with normal behavior and flag anything that seems strange. This can help catch new types of attacks, though it can sometimes flag harmless activity as suspicious.
Stateful Protocol Analysis IDPS
This method looks at how protocols in the network work. It checks if protocols are being used correctly and helps identify attacks that might get around other systems.
How IDPS Works
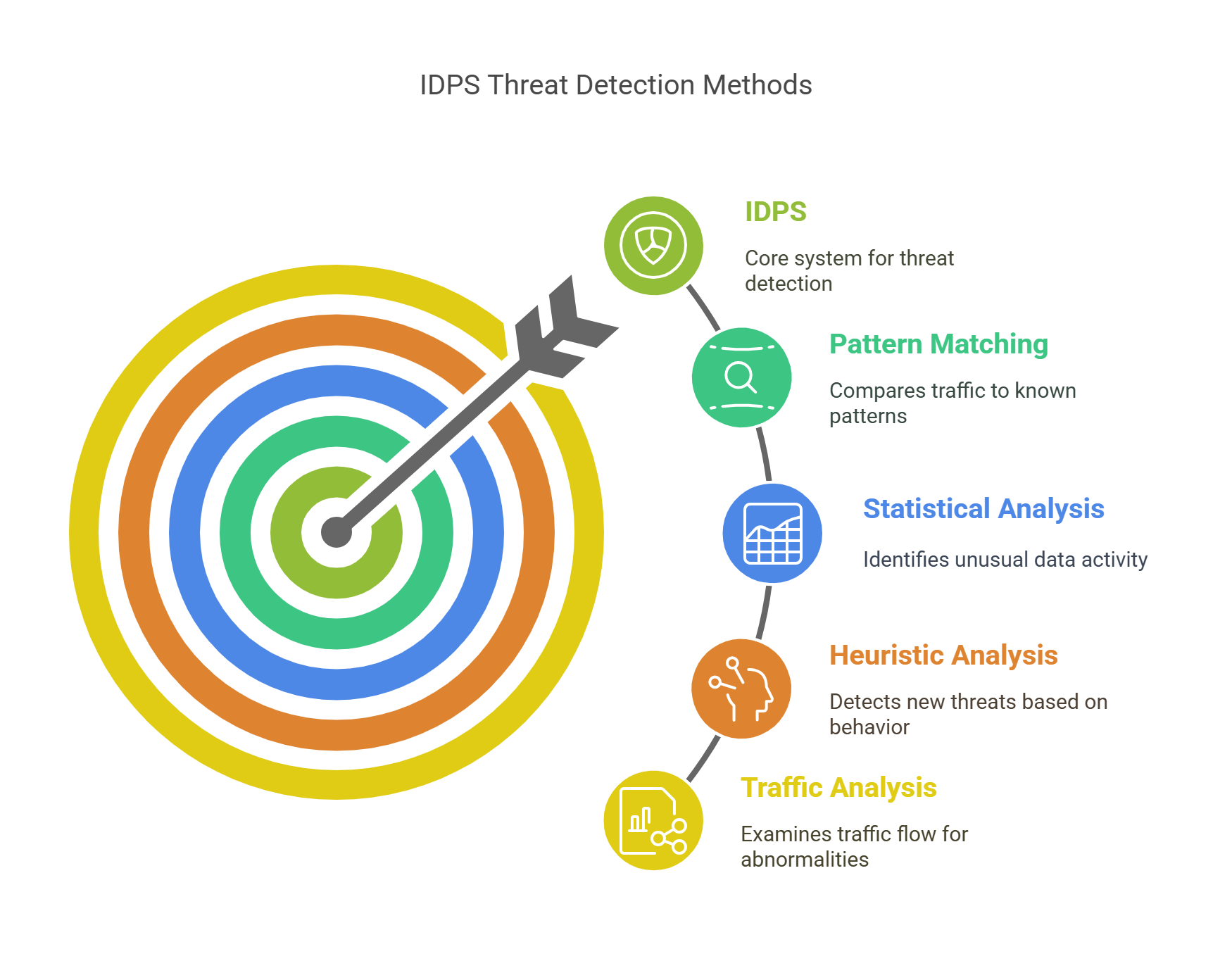
Detection Methods
IDPS systems use several methods to detect threats:
-
Pattern Matching: This compares incoming traffic to known attack patterns.
-
Statistical Analysis: This looks for unusual activity in the data.
-
Heuristic Analysis: This uses algorithms to detect new threats based on their behavior.
-
Traffic Analysis: This examines the flow of traffic to find abnormal patterns.
Prevention Methods
When IDPS detects a threat, it takes action to stop it:
-
Blocking Traffic: The system blocks harmful traffic by stopping certain IP addresses or ports.
-
Session Termination: It can disconnect an active session if an attack is happening.
-
Alerting: If the threat is less serious, the system will alert the administrator.
Why Use IDPS?
Real-Time Monitoring
IDPS allows businesses to monitor activity as it happens. This lets them respond quickly to potential threats, reducing damage.
Preventing Data Breaches
IDPS helps prevent data breaches by detecting threats before they can harm sensitive data.
Comprehensive Protection
IDPS systems protect against a wide range of threats, like DDoS attacks, malware, and SQL injections. They provide multiple layers of protection for both businesses and individuals.
Reducing Human Error
IDPS automates the detection and prevention of threats, reducing the chance of human error. Security teams no longer have to manually monitor network traffic.
Regulatory Compliance
Many industries are required to follow security standards, like HIPAA or GDPR. IDPS helps companies meet these standards by protecting sensitive data.
Choosing the Right IDPS
When picking an IDPS for your company, here are some things to think about:
1. Understand Your Needs
What kind of monitoring do you need: network, host, or both? Also, consider the types of traffic and applications your organization uses.
2. Choose Detection Methods
Decide if you need signature-based or anomaly-based detection. Choose the method that works best for the types of threats you worry about.
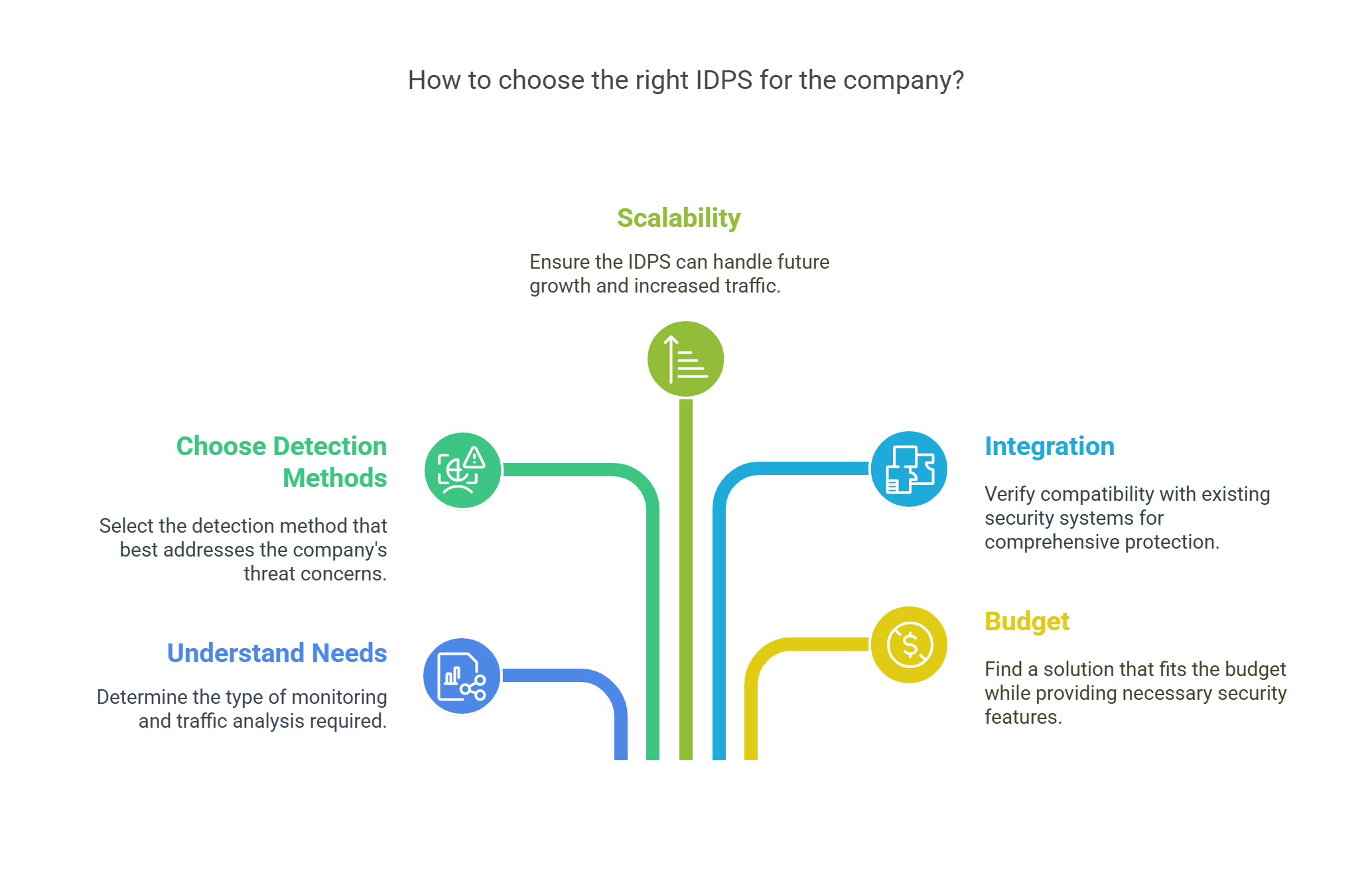
3. Scalability
Make sure the IDPS can grow with your business. As your company expands, the system should handle more traffic and more complex security needs.
4. Integration
Make sure the IDPS can work with your current security systems, such as SIEM (Security Information and Event Management) systems, for better protection.
5. Budget
While IDPS is important for security, the cost can vary. Compare different solutions and find one that fits your budget while providing the protection you need.
FAQ:
What’s the difference between IDS and IDPS?
An IDS (Intrusion Detection System) detects threats and sends alerts, while an IDPS (Intrusion Prevention System) does the same but also takes action to block or stop the threats.
Can IDPS detect all threats?
IDPS systems can catch many threats, but they may not detect newer or more complex ones. It’s best to use multiple layers of protection.
Are IDPS systems hard to manage?
Modern IDPS systems are user-friendly, but they need regular updates and monitoring to stay effective.
Conclusion
IDPS plays an important role in keeping your network safe from cyberattacks. As threats become more advanced, it’s crucial to have a system in place to protect your data. By choosing the right IDPS and understanding how it works, you can improve your organization’s security.
Explore top-rated IDPS solutions today and improve your cybersecurity to protect your valuable digital assets.