The digital world of 2025 is more connected than ever, offering great opportunities but also serious risks. Cyber threats have become more advanced, targeting people, businesses, and governments. Knowing these threats is key to staying safe online. This guide looks at the top digital dangers of 2025 and how to protect against them.
The Changing Cyber Threats
Cyberattacks are now more complex and often backed by governments. Artificial intelligence (AI) helps attackers act faster and smarter. Tensions between countries have led to more cyber warfare, with attacks on important systems like water plants and hospitals. In 2024, ransomware attacks on U.S. infrastructure increased by 9%, showing the growing danger.
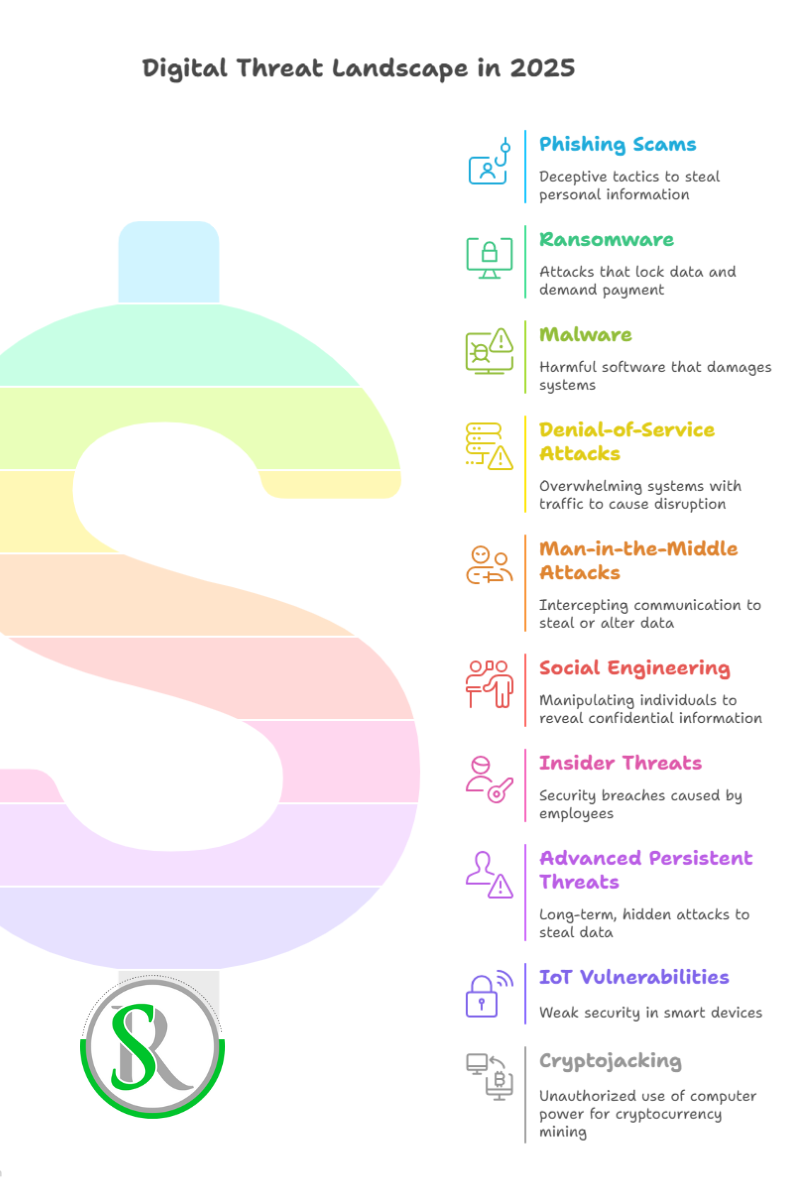
Top 10 Digital Threats in 2025
1. Phishing Scams
Phishing tricks people into giving away personal information through fake emails or websites. AI makes these scams more believable and harder to spot.
2. Ransomware
Ransomware locks your data and demands money to unlock it. These attacks now target crucial services like hospitals and factories. The FBI reported a 9% increase in such attacks in 2024.
3. Malware
Malware is harmful software that can damage or access your computer without permission. AI helps create smarter malware that avoids detection.
4. Denial-of-Service (DoS) Attacks
DoS attacks flood systems with traffic, making them unusable. They can shut down websites and are sometimes used to distract from other attacks.
5. Man-in-the-Middle (MitM) Attacks
In MitM attacks, hackers secretly intercept communication between two parties, stealing or altering information.
6. Social Engineering
This involves tricking people into giving up confidential information. Techniques include pretending to be someone trustworthy or offering fake rewards.
7. Insider Threats
Sometimes, employees or insiders cause security breaches, either by accident or on purpose.
8. Advanced Persistent Threats (APTs)
APTs are long-term attacks where hackers stay hidden in a system to steal data over time. These are often carried out by state-sponsored groups.
9. IoT Vulnerabilities
Many smart devices lack strong security, making them easy targets for hackers.
10. Cryptojacking
Cryptojacking uses your computer’s power to mine cryptocurrency without your knowledge, slowing down your system.
New Threats Emerging
AI-Powered Attacks
Cybercriminals use AI to automate attacks, create fake content, and develop smarter malware. These AI-driven threats are harder to detect.
Deepfakes and Fake Media
Deepfakes are fake videos or audio made using AI. They can spread false information or impersonate people. In early 2025, deepfake scams caused over $200 million in losses.
Supply Chain Attacks
Hackers target suppliers to access larger networks. A major breach in Oracle Cloud affected over 140,000 clients, showing the widespread impact.
How to Stay Safe
Strong Security Measures
-
Keep Software Updated: Regular updates fix security holes.
-
Use Firewalls and Antivirus: These tools help block threats.
-
Enable Multi-Factor Authentication (MFA): Adds an extra layer of security to logins.
Employee Training
Teach staff to recognize phishing and handle data properly.
Regular Security Checks
Conduct audits to find and fix security weaknesses.
Incident Response Plan
Have a clear plan to respond to security breaches, including steps to contain and recover.
FAQs
Q1: What is the most common digital threat in 2025?
Phishing scams are still the most widespread, using advanced techniques to trick users.
Q2: How can I protect my business from ransomware?
Regularly back up data, keep security software updated, and train employees to spot suspicious emails.
Q3: What are deepfakes, and why are they dangerous?
Deepfakes are fake videos or audio created using AI. They can spread false information and impersonate individuals, leading to fraud and misinformation.


